首页 > 最新消息 >[Carbon Black FAQ] 认识 Cb Response 的威胁情资
最新消息
2017-12-14
[Carbon Black FAQ] 认识 Cb Response 的威胁情资

新世代端点防护品牌Carbon Black内建21个威胁情资来源,画面范例如下:
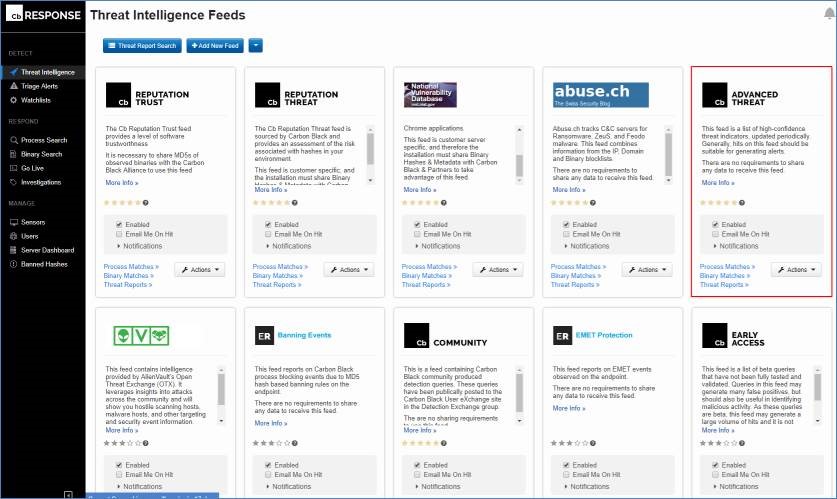
其中具有 Cb Logo 的,是 Carbon Black 自己提供的威胁情资。每个都有不同的目的与应用,以右上角的 Cb Advanced Threat 为例,是设计来针对各种 APT 的攻击手法(TTP)进行收集情资。
Q: Cb Advanced Threat威胁情资里面有哪些内容呢?
A: 下面网址呈现了该威胁情资的内容摘要,该情资每天会更新内容。
https://www.carbonblack.com/cbfeeds/advancedthreat_feed.xhtml
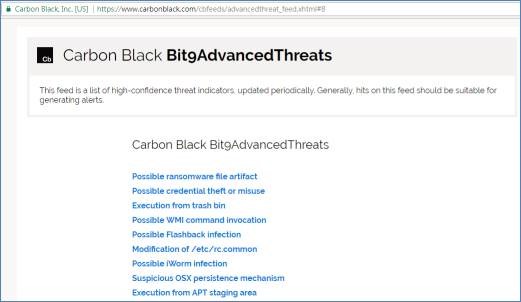
该情资目前有 58 条手法、议题,都是 APT 活动的可能迹象。
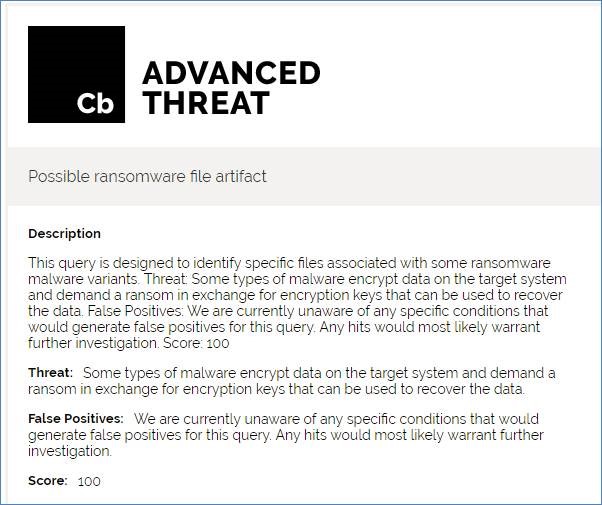
以其中第一条 Possible ransomware file artifact勒索软体相关的档案迹象为例,画面说明如下。
其中也会说明这条情资规则的分数,以及是否可能会造成误判。
下面列出目前 Cb Advanced Threat 威胁情资的58种项目条列 (2017-12-14 为止)
- Possible ransomware file artifact
- Possible credential theft or misuse
- Execution from trash bin
- Possible WMI command invocation
- Possible Flashback infection
- Modification of /etc/rc.common
- Possible iWorm infection
- Suspicious OSX persistence mechanism
- Execution from APT staging area
- Possible wirenet and/or netweird activity
- Suspicious process name
- Possible WireLurker infection
- Processes with obfuscated extensions
- Possible malicious powershell activity
- Possible ZeroAccess activity
- Possible BlackPOS malware registry artifact
- WinRM command activity
- Attempted OSX password hash collection
- Execution from System Volume Information folder
- Known malware file name
- Possible Olyx/Lasyr activity
- Modification of powershell execution policy
- Possible Point-of-sale malware file artifact
- Powershell executed with encoded instructions
- Operation Blockbuster query
- Possible WMI Persistence
- Suspicious local password change
- Possible APT backdoor installation
- Possible Tibet.c backdoor installation
- Suspicious process execution
- Modification of launchd.conf
- Suspicious shell activity
- Execution from Recycle Bin
- ntvdm.exe spawned by office application
- Proxy Modifications By Shell/Script Process
- Retefe Child Processes
- WinVerifyTrust Abuse
- Powershell Running MimiKatz
- Attempted Whitelisting Bypass
- NotPetya Filemods
- Unusual RunDll Child AcceptEula
- Unusual RunDll Child Scheduled Tasks
- Disguised Psexec - Internal Name
- Notepad and MSDCSC Launched
- WMI Launching MSHTA Launching Script Interpreters
- File Deletion With Ping
- Changes to Known DLLs registry
- Run Key Added With Suspicious Value Path
- RegSvr32 Making Network Connections
- Word Spawning Command Process
- Process Spawning Both Notepad and Vssadmin
- Process Running From Tasks Directory
- Process Running From Debug Directory
- Lsass Writing Binaries to Disk
- Services null Instance registry key
- Known Bad Child Processes of Lsass
- Bad Rabbit - Tricks are for Kids
- MS Office Vuln - CVE-2017-11882 – query
Q: Cb 的威胁情资多久会更新一次?
A: 每个威胁情资依据其属性与资料来源不同,有些是几分钟更新一次,有些是一天更新一次。
更新的模式,预设都是 Incremental Update/差异式更新,
一旦新的情资被更新到 Db Response Server,
马上会对主机中对单位内所有端点收集到的历史资料进行比对。
触发时可以产生 Alert ,也可以设定 Email通知或启动 Syslog 事件传送。



